Cyber Security Awareness for Dummies
Table of ContentsCyber Security Awareness for DummiesThe Ultimate Guide To Cyber Security AwarenessAbout Cyber Security AwarenessAn Unbiased View of Cyber Security Awareness
Enhanced entry points for assaults, such as with the arrival of the web of things (Io, T), boost the requirement to secure networks as well as devices. Among the most troublesome components of cybersecurity is the developing nature of security risks. As brand-new technologies emerge, and as modern technology is utilized in new or various means, brand-new assault avenues are established. CISO jobs vary extensively to preserve venture cybersecurity. IT experts as well as various other computer specialists are needed in protection roles, such as: is the person who applies the protection program across the organization and also manages the IT safety and security department's operations. is the exec responsible for the physical and/or cybersecurity of a business.
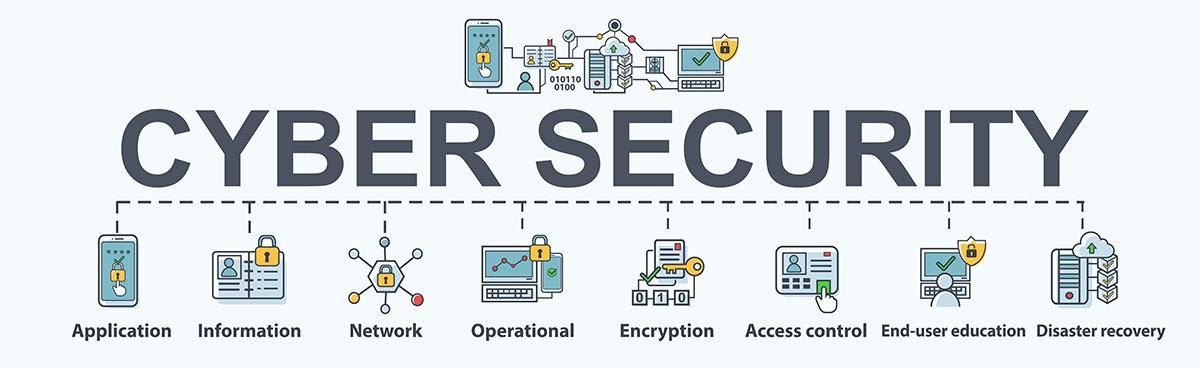
A jeopardized application could offer accessibility to the information its designed to secure. Effective protection starts in the design phase, well prior to a program or tool is deployed.
The consents users have when accessing a network and also the treatments that establish how and also where data may be stored or shared all autumn under this umbrella. specify just how a company reacts to a cyber-security event or any type of various other event that creates the loss of operations or information. Disaster recovery plans dictate how the organization restores its procedures and also details to go back to the very same operating capability as before the occasion.
The Ultimate Guide To Cyber Security Awareness
Cybercriminals deceive customers right into posting Trojans onto their computer where they trigger damage or accumulate information. A program that privately tapes what a user does, to ensure that cybercriminals can utilize this details. For instance, spyware can capture charge card details. Malware which locks down an individual's data as well as information, with the risk of erasing it unless a ransom money is paid.

This indicates you benefit from the newest security patches. Maintain your software updated for the finest degree of protection. This is a common method that malware is spread out.
Network security is the process of protecting the functionality as well as honesty of your network and also data., which examines your network for vulnerabilities and protection concerns.
What Does Cyber Security Awareness Do?
This is because a lot of these services: Can not pay for professional IT services Have limited time to commit to cyber security Don't recognize where to start Below are several of one of the most common risks among cyber assaults:: Malware, also referred to as harmful software, is intrusive software Full Report application established by cyber offenders to take information or to damage and also damage computer systems and computer system systems, according to CISCO.
Right here are the most usual sorts of cyber security offered:: Application safety and security explains safety and security utilized by applications to stop information or code within the application from being stolen or pirated. These safety and security systems are implemented throughout application growth however are developed to shield the application after deployment, according to VMWare.
The Io, T is a network of linked things and people, all of which share information about the means they are utilized as well as their settings, according to IBM., security is one of the most significant obstacles to widespread Io, T adaption.
Fascination About Cyber Security Awareness
Petitto always wished to work within the IT field, as well as he selected cyber safety due to the fact that it's a significantly growing field. He transferred debts from a community college with an U.S. Air Force program as well as completed his bachelor's in under two years. "It was much quicker than I thought it would certainly be," he stated.
"Also prior to ending up (my) level, I got numerous welcomes to talk to for entry-level positions within the industry as well as obtained three work offers," claimed Petitto. He decided to remain within the Air Force and transfer to a cyber security unit as opposed to signing he has a good point up with the personal market.
That's more than twice as fast as the average computer-related line of work as well as four times as rapid as American tasks in basic., a job funded by the federal government and sustained by market partners, offers comprehensive information on the demand for these workers by state.
Bigger firms might have entire divisions committed to shielding info and also chasing after down risks. While business define roles associated to information protection in a range of ways, Kamyck claimed there are some details tasks that these staff members are typically my link gotten in touch with to do. In most cases, they need to evaluate hazards and gather info from a firm's web servers, cloud services and also employee computer systems as well as mobile gadgets (Cyber Security Awareness).